
- Email support@dumps4free.com

Topic 1: Exam Pool A
In the field of cryptanalysis, what is meant by a “rubber-hose” attack?
A.
Forcing the targeted keystream through a hardware-accelerated device such as an
ASIC.
B.
A backdoor placed into a cryptographic algorithm by its creator
C.
Extraction of cryptographic secrets through coercion or torture
D.
Attempting to decrypt ciphertext by making logical assumptions about the contents of
the original plaintex
Extraction of cryptographic secrets through coercion or torture
A powerful and often the most effective cryptanalysis method in which the
attack is directed at the most vulnerable link in the cryptosystem - the person. In this attack,
the cryptanalyst uses blackmail, threats, torture, extortion, bribery, etc. This method's main
advantage is the decryption time's fundamental independence from the volume of secret
information, the length of the key, and the cipher's mathematical strength.
The method can reduce the time to guess a password, for example, for AES, to an
acceptable level; however, it requires special authorization from the relevant regulatory
authorities. Therefore, it is outside the scope of this course and is not considered in its
practical part.
The change of a hard drive failure is once every three years. The cost to buy a new hard
drive is $300. It will require 10 hours to restore the OS and software to the new hard disk. It
will require a further 4 hours to restore the database from the last backup to the new hard
disk. The recovery person earns $10/hour. Calculate the SLE, ARO, and ALE. Assume the
EF = 1(100%). What is the closest approximate cost of this replacement and recovery
operation per year?
A.
$1320
B.
$440
C.
$100
D.
$146
$146
Explanation: 1. AV (Asset value) = $300 + (14 * $10) = $440 - the cost of a hard drive
plus the work of a recovery person, i.e.how much would it take to replace 1 asset? 10
hours for resorting the OS and soft + 4 hours for DB restore multiplies by hourly rate of the
recovery person.
2. SLE (Single Loss Expectancy) = AV * EF (Exposure Factor) = $440 * 1 = $440
3. ARO (Annual rate of occurrence) = 1/3 (every three years, meaning the probability of
occurring during 1 years is 1/3)
4. ALE (Annual Loss Expectancy) = SLE * ARO = 0.33 * $440 = $145.2
Study the snort rule given below:
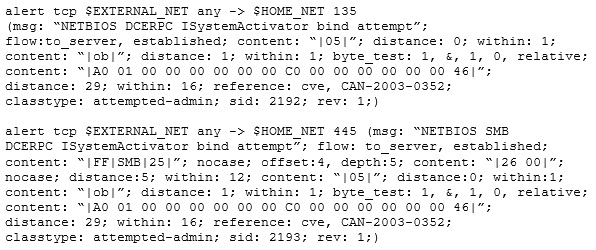
From the options below, choose the exploit against which this rule applies.
A.
WebDav
B.
SQL Slammer
C.
MS Blaster
D.
MyDoom
MS Blaster
Why should the security analyst disable/remove unnecessary ISAPI filters?
A.
To defend against social engineering attacks
B.
To defend against webserver attacks
C.
To defend against jailbreaking
D.
To defend against jailbreaking
To defend against webserver attacks
Identify the UDP port that Network Time Protocol (NTP) uses as its primary means of
communication?
A.
113
B.
69
C.
123
D.
161
123
Explanation:
https://en.wikipedia.org/wiki/Network_Time_Protocol
The Network Time Protocol (NTP) is a networking protocol for clock synchronization
between computer systems over packet-switched, variable-latency data networks.
NTP is intended to synchronize all participating computers within a few milliseconds of
Coordinated Universal Time (UTC). It uses the intersection algorithm, a modified version of
Marzullo's algorithm, to select accurate time servers and is designed to mitigate variable
network latency effects. NTP can usually maintain time to within tens of milliseconds over
the public Internet and achieve better than one millisecond accuracy in local area networks.
Asymmetric routes and network congestion can cause errors of 100 ms or more.
The protocol is usually described in terms of a client-server model but can easily be used in
peer-to-peer relationships where both peers consider the other to be a potential time
source. Implementations send and receive timestamps using the User Datagram Protocol
(UDP) on port number 123.
| Page 11 out of 114 Pages |
| Previous |