
- Email support@dumps4free.com

Henry Is a cyber security specialist hired by BlackEye - Cyber security solutions. He was
tasked with discovering the operating system (OS) of a host. He used the Unkornscan tool
to discover the OS of the target system. As a result, he obtained a TTL value, which
Indicates that the target system is running a Windows OS. Identify the TTL value Henry
obtained, which indicates that the target OS is Windows.
A.
A6
B.
128
C.
255
D.
138
128
Bob was recently hired by a medical company after it experienced a major cyber security
breach. Many patients are complaining that their personal medical records are fully
exposed on the Internet and someone can find them with a simple Google search. Bob's
boss is very worried because of regulations that protect those data. Which of the following
regulations is mostly violated?
A.
HIPPA/PHl
B.
Pll
C.
PCIDSS
D.
ISO 2002
Pll
If a tester is attempting to ping a target that exists but receives no response or a response
that states the destination is unreachable, ICMP may be disabled and the network may be
using TCP. Which other option could the tester use to get a response from a host using
TCP?
A.
Traceroute
B.
Hping
C.
TCP ping
D.
Broadcast ping
Hping
When a security analyst prepares for the formal security assessment - what of the following
should be done in order to determine inconsistencies in the secure assets database andverify that system is compliant to the minimum security baseline?
A.
Data items and vulnerability scanning
B.
Interviewing employees and network engineers
C.
Reviewing the firewalls configuration
D.
Source code review
Data items and vulnerability scanning
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c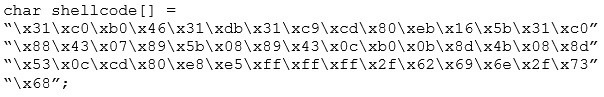
What is the hexadecimal value of NOP instruction?
A.
0x60
B.
0x80
C.
0x70
D.
0x90
0x90
| Page 31 out of 104 Pages |
| Previous |