
- Email support@dumps4free.com

Bob, an attacker, has managed to access a target loT device. He employed an online tool
to gather information related to the model of the loT device and the certifications granted to
it. Which of the following tools did Bob employ to gather the above Information?
A.
search.com
B.
EarthExplorer
C.
Google image search
D.
FCC ID search
FCC ID search
You are tasked to configure the DHCP server to lease the last 100 usable IP addresses in
subnet to. 1.4.0/23. Which of the following IP addresses could be teased as a result of the
new configuration?
A.
210.1.55.200
B.
10.1.4.254
C.
10..1.5.200
D.
10.1.4.156
10..1.5.200
ViruXine.W32 virus hides their presence by changing the underlying executable code.
This Virus code mutates while keeping the original algorithm intact, the code changes itself
each time it runs, but the function of the code (its semantics) will not change at all.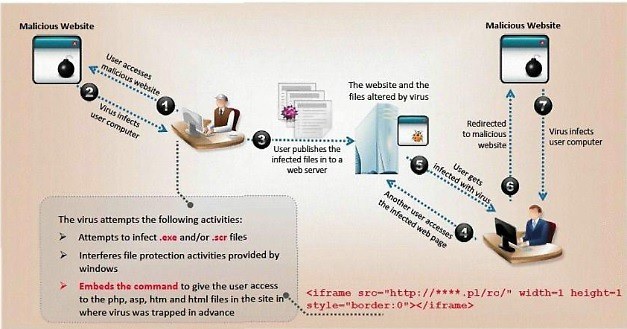
What is this technique called?
A.
Polymorphic Virus
B.
Metamorphic Virus
C.
Dravidic Virus
D.
Stealth Virus
Polymorphic Virus
Which method of password cracking takes the most time and effort?
A.
Dictionary attack
B.
Shoulder surfing
C.
Rainbow tables
D.
Brute force
Brute force
A new wireless client is configured to join a 802.11 network. This client uses the same
hardware and software as many of the other clients on the network. The client can see the
network, but cannot connect. A wireless packet sniffer shows that the Wireless Access
Point (WAP) is not responding to the association requests being sent by the wireless client.
What is a possible source of this problem?
A.
The WAP does not recognize the client’s MAC address
B.
The client cannot see the SSID of the wireless network
C.
Client is configured for the wrong channel
D.
The wireless client is not configured to use DHCP
The WAP does not recognize the client’s MAC address
| Page 18 out of 104 Pages |
| Previous |