
- Email support@dumps4free.com

Switches maintain a CAM Table that maps individual MAC addresses on the network to physical ports on the switch.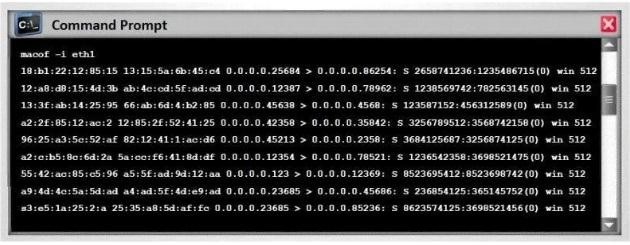
In MAC flooding attack, a switch is fed with many Ethernet frames, each containing
different source MAC addresses, by the attacker. Switches have a limited memory for
mapping various MAC addresses to physical ports. What happens when the CAM table
becomes full?
A.
Switch then acts as hub by broadcasting packets to all machines on the network
B.
The CAM overflow table will cause the switch to crash causing Denial of Service
C.
The switch replaces outgoing frame switch factory default MAC address of
FF:FF:FF:FF:FF:FF
D.
Every packet is dropped and the switch sends out SNMP alerts to the IDS port
Switch then acts as hub by broadcasting packets to all machines on the network
You are tasked to perform a penetration test. While you are performing information
gathering, you find an employee list in Google. You find the receptionist’s email, and you
send her an email changing the source email to her boss’s email (boss@company). In this
email, you ask for a pdf with information. She reads your email and sends back a pdf with
links. You exchange the pdf links with your malicious links (these links contain malware)
and send back the modified pdf, saying that the links don’t work. She reads your email,
opens the links, and her machine gets infected. You now have access to the company
network. What testing method did you use?
A.
Social engineering
B.
Piggybacking
C.
Tailgating
D.
Eavesdropping
Social engineering
Study the following log extract and identify the attack 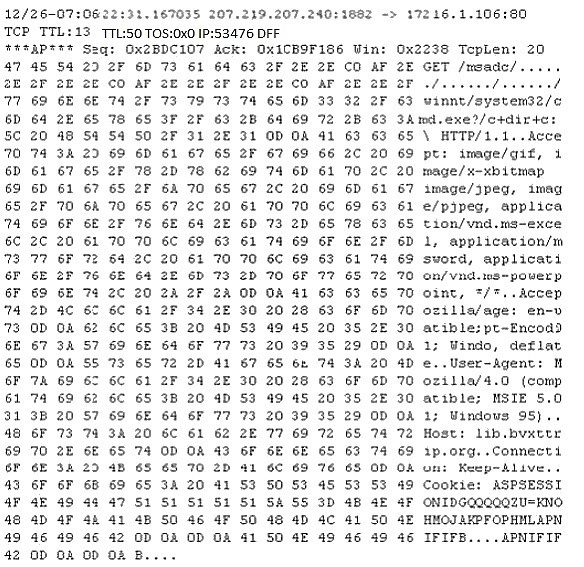
A.
Hexcode Attack
B.
Cross Site Scripting
C.
Multiple Domain Traversal Attack
D.
Unicode Directory Traversal Attack
Unicode Directory Traversal Attack
One of your team members has asked you to analyze the following SOA record.
What is the TTL? Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600 3600 604800 2400.)
A.
200303028
B.
3600
C.
604800
D.
2400
E.
60
F.
4800
2400
Techno Security Inc. recently hired John as a penetration tester. He was tasked with
identifying open ports in the target network and determining whether the ports are online
and any firewall rule sets are encountered. John decided to perform a TCP SYN ping scan
on the target network. Which of the following Nmap commands must John use to perform
the TCP SVN ping scan?
A.
nmap -sn -pp < target ip address >
B.
nmap -sn -PO < target IP address >
C.
Anmap -sn -PS < target IP address >
D.
nmap -sn -PA < target IP address >
Anmap -sn -PS < target IP address >
| Page 1 out of 104 Pages |