
- Email support@dumps4free.com

Topic 1: Exam Set A
A mobile operating system manages communication between the mobile device and other
compatible devices like computers, televisions, or printers.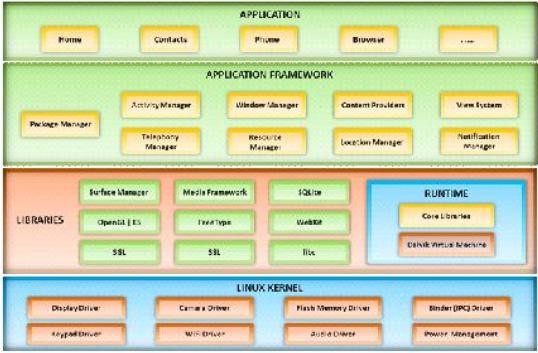
Which mobile operating system architecture is represented here?
A.
webOS System Architecture
B.
Symbian OS Architecture
C.
Android OS Architecture
D.
Windows Phone 7 Architecture
Android OS Architecture
TCP/IP (Transmission Control Protocol/Internet Protocol) is a communication protocol used
to connect different hosts in the Internet. It contains four layers, namely the network
interface layer. Internet layer, transport layer, and application layer.
Which of the following protocols works under the transport layer of TCP/IP?
A.
UDP
B.
HTTP
C.
FTP
D.
SNMP
UDP
Computer security logs contain information about the events occurring within an
organization's systems and networks. Which of the following security logs contains Logs of
network and host-based security software?
A.
Operating System (OS) logs
B.
Application logs
C.
Security software logs
D.
Audit logs
Security software logs
What is the First Step required in preparing a computer for forensics investigation?
A.
Do not turn the computer off or on, run any programs, or attempt to access data on a
computer
B.
Secure any relevant media
C.
Suspend automated document destruction and recycling policies that may pertain to any
relevant media or users at Issue
D.
Identify the type of data you are seeking, the Information you are looking for, and the
urgency level of the examination
Do not turn the computer off or on, run any programs, or attempt to access data on a
computer
In an echo data hiding technique, the secret message is embedded into a __________as
an echo.
A.
Cover audio signal
B.
Phase spectrum of a digital signal
C.
Pseudo-random signal
D.
Pseudo- spectrum signal
Cover audio signal
| Page 13 out of 98 Pages |
| Previous |