
- Email support@dumps4free.com

Properly applied cyber threat intelligence to the SOC team help them in discovering TTPs. What does these TTPs refer to?
A.
Tactics, Techniques, and Procedures
B.
Tactics, Threats, and Procedures
C.
Targets, Threats, and Process
D.
Tactics, Targets, and Process
Tactics, Techniques, and Procedures
Reference: https://www.crest-approved.org/wp-content/uploads/CREST-Cyber-Threat-
Intelligence.pdf
David is a SOC analyst in Karen Tech. One day an attack is initiated by the intruders but David was not able to find any suspicious events. This type of incident is categorized into?
A.
True Positive Incidents
B.
False positive Incidents
C.
True Negative Incidents
D.
False Negative Incidents
True Negative Incidents
An organization is implementing and deploying the SIEM with following capabilities.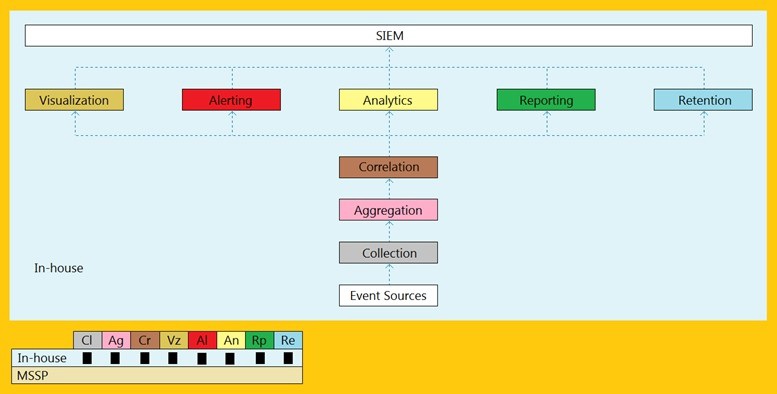
What kind of SIEM deployment architecture the organization is planning to implement?
A.
Cloud, MSSP Managed
B.
Self-hosted, Jointly Managed
C.
Self-hosted, Self-Managed
D.
Self-hosted, MSSP Managed
Cloud, MSSP Managed
In which log collection mechanism, the system or application sends log records either on the local disk or over the network.
A.
rule-based
B.
pull-based
C.
push-based
D.
signature-based
rule-based
Chloe, a SOC analyst with Jake Tech, is checking Linux systems logs. She is investigating
files at /var/log/ wtmp.
What Chloe is looking at?
A.
Error log
B.
System boot log
C.
General message and system-related stuff
D.
Login records
Login records
| Page 3 out of 21 Pages |
| Previous |