
- Email support@dumps4free.com

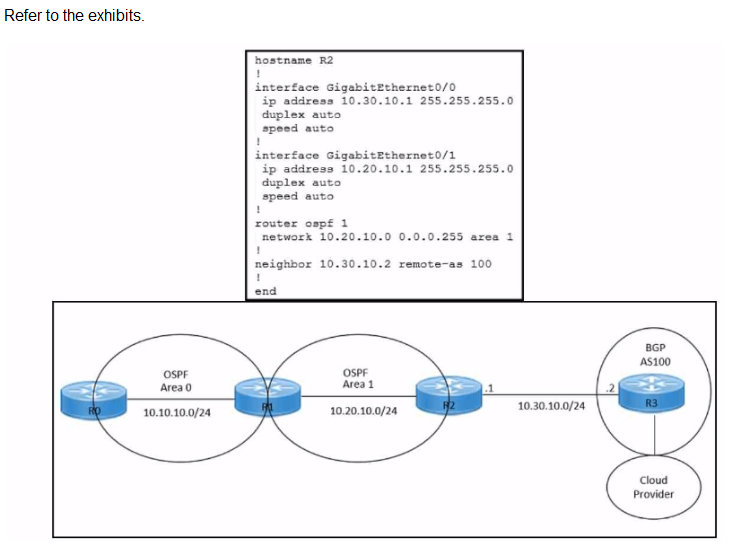
An engineer must redistribute IBGP routes into OSPF to connect an
on-premises network to a cloud provider. Which command must be configured on router
R2?
A. redistribute ospf 1
B. redistribute bgp 100 ospf 1
C. redistribute bgp 100 subnets
D. bgp redistrlbute-lnternal
Explanation: This command redistributes the routes learned from BGP AS100 into OSPF Area1, which allows router R2 to advertise those routes to router R1 and connect the on-premises network to the cloud provider. The other options are incorrect because they either redistribute the wrong routes or use the wrong syntax5. I hope this helps you understand the question and the answer. If you have any other questions or requests, please let me know. I am always happy to help.
A cloud engineer is setting up a new set of nodes in the AWS EKS cluster to manage database integration with Mongo Atlas. The engineer set up security to Mongo but now wants to ensure that the nodes are also secure on the network side. Which feature in AWS should the engineer use?
A. EC2 Trust Lock
B. security groups
C. tagging
D. key pairs
Explanation: Security groups are a feature in AWS that allow you to control the inbound and outbound traffic to your instances. They act as a virtual firewall that can filter the traffic based on the source, destination, protocol, and port. You can assign one or more security groups to your instances, and each security group can have multiple rules. Security groups are stateful, meaning that they automatically allow the response traffic for any allowed inbound traffic, and vice versa. Security groups are essential for securing your nodes in the AWS EKS cluster, as they can prevent unauthorized access to your Mongo Atlas database or other resources. You can also use security groups to isolate your nodes from other instances in the same VPC or subnet, or to allow communication between nodes in different clusters or regions.
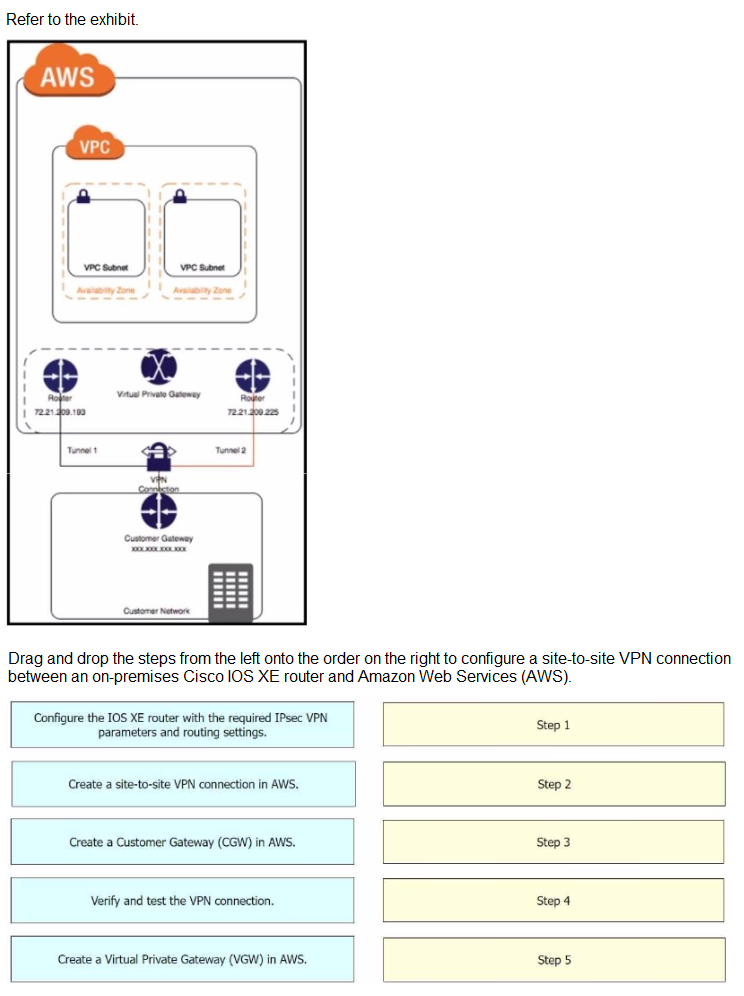
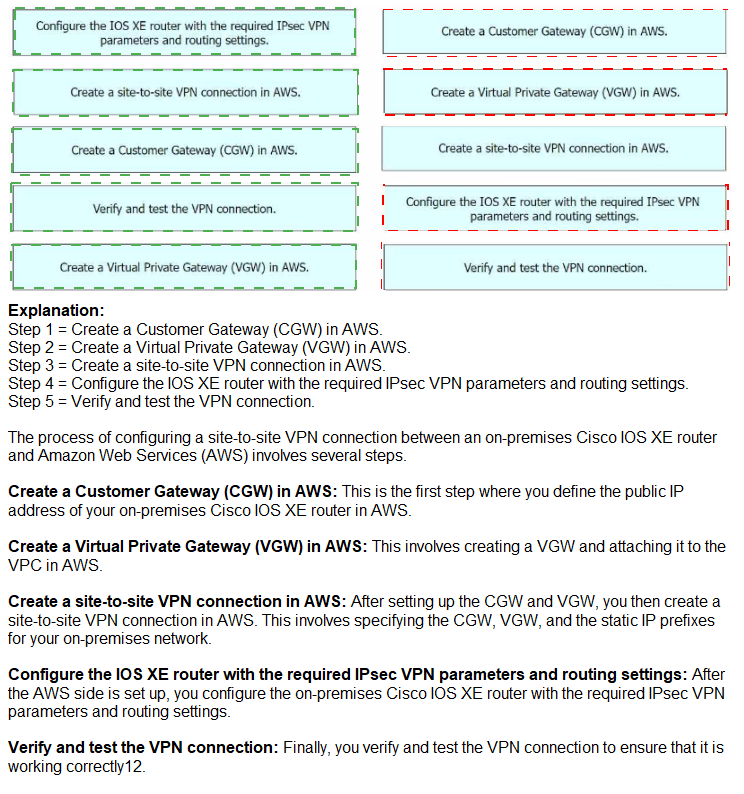
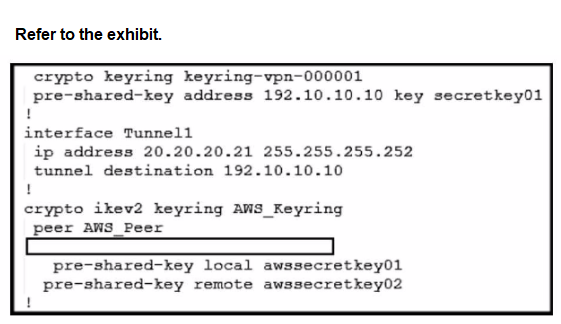
An engineer needs to configure a site-to-site IPsec VPN connection
between an on-premises Cisco IOS XE router and Amazon Web Services (AWS). Which
configuration command must be placed in the blank in the code to complete the tunnel
configuration?
A. address 20.20.20.21
B. address 192.10.10.10
C. tunnel source 20.20.20.21
D. tunnel source 192.10.10.10
Explanation: In the given scenario, an engineer is configuring a site-to-site IPsec VPN connection between an on-premises Cisco IOS XE router and AWS. The correct command to complete the tunnel configuration is “tunnel source 20.20.20.21”. This command specifies the source IP address for the tunnel, which is essential for establishing a secure connection between two endpoints over the internet or another network1.
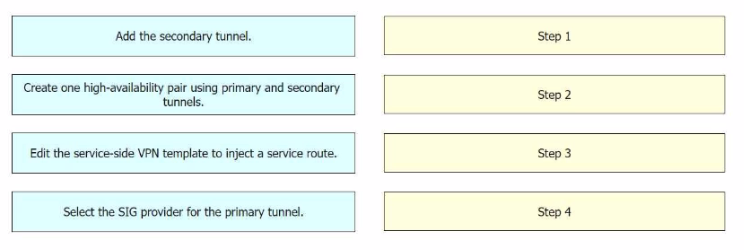
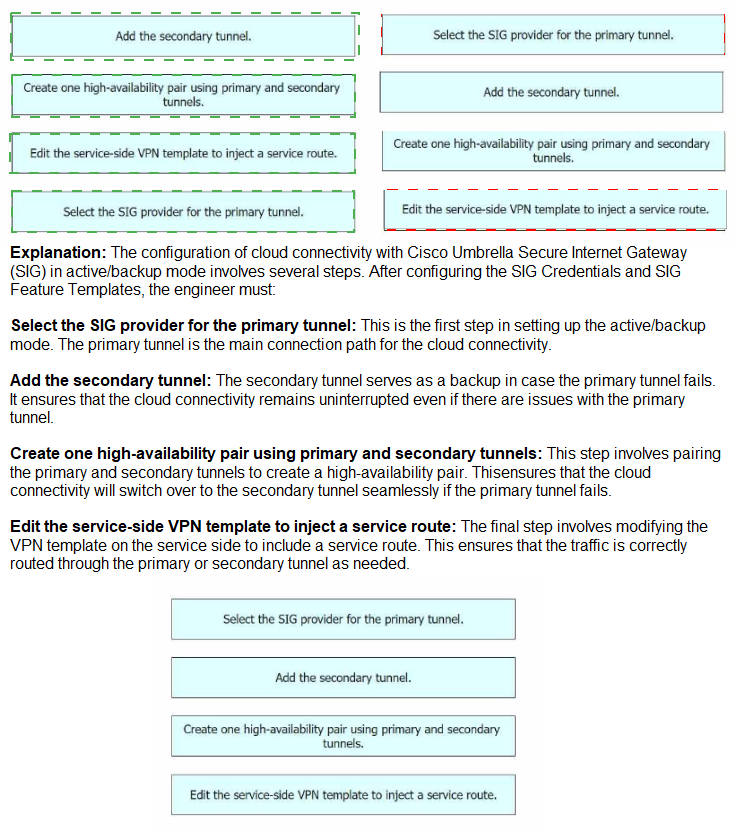
An engineer must configure cloud connectivity with Cisco Umbrella Secure Internet Gateway (SIG) in active/backup mode. The engineer already configured the SIG Credentials and SIG Feature Templates. Drag and drop the steps from the left onto the order on the right to complete the configuration.
| Page 2 out of 8 Pages |
| Previous |