
- Email support@dumps4free.com

Topic 2, Exam Pool B
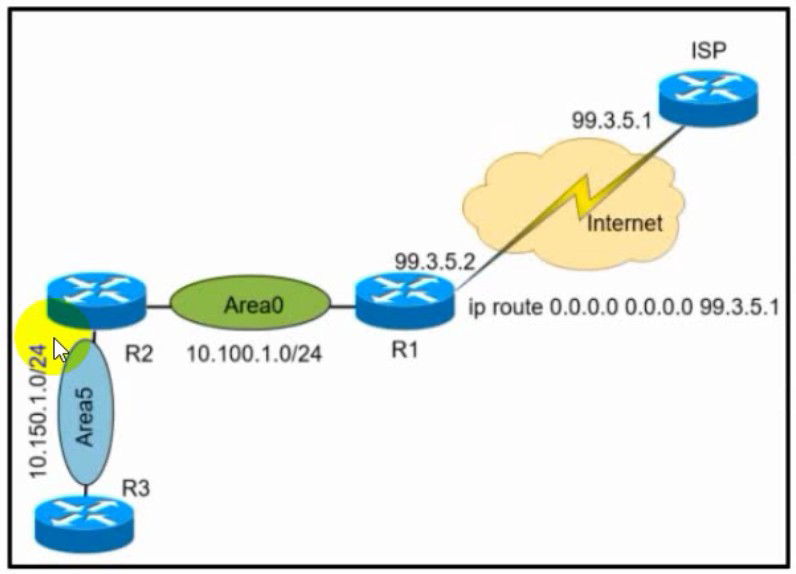
Refer to the exhibit. A network administrator redistributed the default static route into OSPF toward all internal routers to reach to Internet. Which set of commands restores reachability to the Internet by internal routers?
A.
router ospf 1
default-information originate
B.
router ospf 1
network 0.0.0.0 0.0.0.0 area 0
C.
router ospf 1
redistribute connected 0.0.0.0
D.
router ospf 1
redistribute static subnets
router ospf 1
default-information originate
Refer to the exhibit.
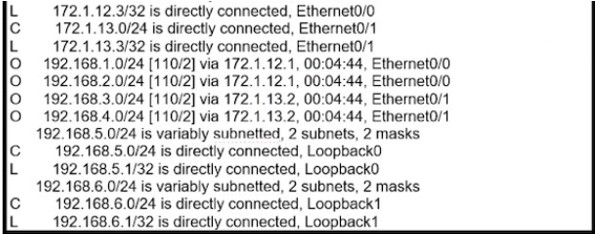
SanFrancisco and Boston routers are choosing slower links to reach each other despite the direct links being up Which configuration fixes the issue?
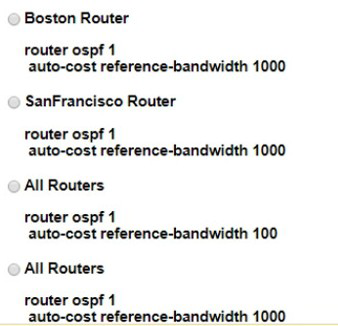
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option D
An engineer configured SNMP notifications sent to the management server using authentication and encrypting data with DES. An error in the response PDU is received as "UNKNOWNUSERNAME. WRONGDIGEST". Which action resolves the issue?
A.
Configure the correct authentication password using SNMPv3 authPriv .
B.
Configure the correct authentication password using SNMPv3 authNoPriv.
C.
Configure correct authentication and privacy passwords using SNMPv3 authNoPriv.
D.
Configure correct authentication and privacy passwords using SNMPv3 authPriv.
Configure correct authentication and privacy passwords using SNMPv3 authPriv.
In which two ways does the IPv6 First-Hop Security Binding Table operate? (Choose two.)
A.
by IPv6 routing protocols to securely build neighborships without the need of authentication
B.
by the recovery mechanism to recover the binding table in the event of a device reboot
C.
by IPv6 HSRP to make sure neighbors are authenticated before being used as gateways
D.
by various IPv6 guard features to validate the data link layer address
E.
by storing hashed keys for IPsec tunnels for the built-in IPsec features
by the recovery mechanism to recover the binding table in the event of a device reboot
by various IPv6 guard features to validate the data link layer address
Explanation:
Overview of the IPv6 First-Hop Security Binding Table A database table of IPv6 neighbors connected to the device is created from information
sources such as NDP snooping. This database, or binding table, is used by variousIPv6 guard features to validate the link-layer address (LLA), the IPv4 or IPv6 address, and the prefix binding of the neighbors to prevent spoofing and redirect attacks.
IPv6 First-Hop Security Binding Table Recovery MechanismThe IPv6 first-hop security binding table recovery mechanism enables the binding table to recover in the event of a device reboot.
When configuring Control Plane Policing on a router to protect it from malicious traffic, an engineer observes that the configured routing protocols start flapping on that device. Which action in the Control Plane Policy prevents this problem in a production environment while achieving the security objective?
A.
Set the conform-action and exceed-action to transmit initially to test the ACLs and transmit rates and apply the Control Plane Policy in the output direction
B.
Set the conform-action and exceed-action to transmit initially to test the ACLs and transmit rates and apply the Control Plane Policy in the input direction
C.
Set the conform-action to transmit and exceed-action to drop to test the ACLs and transmit rates and apply the Control Plane Policy m the input direction
D.
Set the conform-action to transmit and exceed-action to drop to test the ACLs and transmit rates and apply the Control Plane Policy m the output direction
Set the conform-action and exceed-action to transmit initially to test the ACLs and transmit rates and apply the Control Plane Policy in the input direction
| Page 39 out of 113 Pages |
| Previous |