
- Email support@dumps4free.com

Topic 1, Exam Pool A
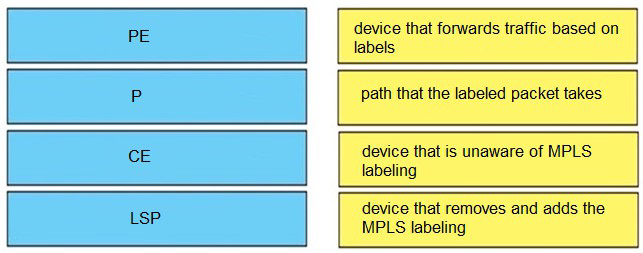
Drag and drop the MPLS terms from the left onto the correct definitions on the right.
Which list defines the contents of an MPLS label?
A.
20-bit label; 3-bit traffic class; 1-bit bottom stack; 8-bit TTL
B.
32-bit label; 3-bit traffic class; 1-bit bottom stack; 8-bit TTL
C.
20-bit label; 3-bit flow label; 1-bit bottom stack; 8-bit hop limit
D.
32-bit label; 3-bit flow label; 1-bit bottom stack; 8-bit hop limit
20-bit label; 3-bit traffic class; 1-bit bottom stack; 8-bit TTL
Explanation: The first 20 bits constitute a label, which can have 2^20 values. Next comes 3 bit value called Traffic Class. It was formerly called as experimental (EXP) field. Now it has been renamed to Traffic Class (TC). This field is used for QoS related functions.
Ingress router can classify the packet according to some criterion and assign a 3 bit value to this filed. If an incoming packet is marked with some IP Precedence or DSCP value and the ingress router may use such a field to assign an FEC to the packet. Next bit is Stack bit which is called bottom-of-stack bit. This field is used when more than one label is assigned to a packet, as in the case of MPLS VPNs or MPLS TE. Next byte is MPLS TTL field which serves the same purpose as that of IP TTL byte in the IP header
Refer to the exhibit.

In which circumstance does the BGP neighbor remain in the idle condition?
A.
if prefixes are not received from the BGP peer
B.
if prefixes reach the maximum limit
C.
if a prefix list is applied on the inbound direction
D.
if prefixes exceed the maximum limit
if prefixes exceed the maximum limit
What is a function of IPv6 ND inspection?
A.
It learns and secures bindings for stateless autoconfiguration addresses in Layer 3 neighbor tables
B.
It learns and secures bindings for stateless autoconfiguration addresses in Layer 2 neighbor tables
C.
It learns and secures bindings for stateful autoconfiguration addresses in Layer 2 neighbor tables.
D.
It learns and secures bindings for stateful autoconfiguration addresses in Layer 3 neighbor tables.
It learns and secures bindings for stateless autoconfiguration addresses in Layer 2 neighbor tables
An engineer is trying to copy an IOS file from one router to another router by using TFTP. Which two actions are needed to allow the file to copy? (Choose two.)
A.
Copy the file to the destination router with the copy tftp: flash: command
B.
Enable the TFTP server on the source router with the tftp-server flash: <filename> command
C.
TFTP is not supported in recent IOS versions, so an alternative method must be used
D.
Configure a user on the source router with the username tftp password tftp command
E.
Configure the TFTP authentication on the source router with the tftp-server authentication local command
Copy the file to the destination router with the copy tftp: flash: command
Enable the TFTP server on the source router with the tftp-server flash: <filename> command
| Page 17 out of 113 Pages |
| Previous |