
- Email support@dumps4free.com

Topic 5: Exam Pool E
A hotel's Wi-Fi was used to steal information on a corporate laptop. A technician notes the following security log:
SRC: 192.168.1.1/secrets.zip Protocol SMB >> DST: 192.168.1.50/capture The technician analyses the following Windows firewall information:
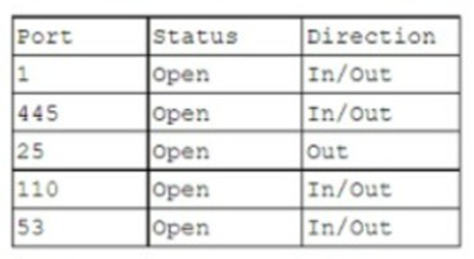
Which of the following protocols most likely allowed the data theft to occur?
A. 1
B. 53
C. 110
D. 445
Explanation: The protocol that most likely allowed the data theft to occur is SMB over TCP port 445. SMB is a network file sharing protocol that enables access to files, printers, and other resources on a network. Port 445 is used by SMB to communicate directly over TCP without the need for NetBIOS, which is an older and less secure protocol. The security log shows that the source IP address 192.168.1.1 sent a file named secrets.zip using SMB protocol to the destination IP address 192.168.1.50, which captured the file. The Windows firewall information shows that port 445 is enabled for inbound and outbound traffic, which means that it is not blocked by the firewall. Therefore, port 445 is the most likely port that was exploited by the attacker to steal the data from the corporate laptop.
An employee has repeatedly contacted a technician about malware infecting a work computer. The technician has removed the malware several times, but the user's PC keeps getting infected. Which of the following should the technician do to reduce the risk of future infections?
A. Configure the firewall.
B. Restore the system from backups.
C. Educate the end user
D. Update the antivirus program.
Explanation: Malware is software that infects computer systems to damage, disable or exploit the computer or network for various malicious purposes5. Malware is typically distributed via email attachments, fake internet ads, infected applications or websites, and often relies on user interaction to execute6. Therefore, one of the most effective ways to prevent malware infections is to educate the end user about the common signs and sources of malware, and how to avoid them7. Configuring the firewall, restoring the system from backups, and updating the antivirus program are also important security measures, but they do not address the root cause of the user’s repeated infections, which is likely due to a lack of awareness or caution.
A customer calls desktop support and begins yelling at a technician. The customer claims to have submitted a support ticket two hours ago and complains that the issue still has not been resolved. Which of the following describes how the technician should respond? Place the customer on hold until the customer calms down.
A. Disconnect the call to avoid a confrontation.
B. Wait until the customer is done speaking and offer assistance.
C. Escalate the issue to a supervisor.
A technician is building a new desktop machine for a user who will be using the workstation to render 3-D promotional movies. Which of the following is the most important component?
A. Dedicated GPU
B. DDR5 SODIMM
C. NVMe disk
D. 64-bit CPU
Which of the following would allow physical access to a restricted area while maintaining a record of events?
A. Hard token
B. Access control vestibule
C. Key fob
D. Door Lock
Explanation: Access control vestibule is the correct answer for this question. An access control vestibule is a physical security device that consists of two doors that form an enclosed space between them. The first door opens only after verifying the identity of the person entering, such as by using a card reader, biometric scanner, or keypad. The second door opens only after the first door closes, creating a buffer zone that prevents unauthorized access or tailgating. An access control vestibule also maintains a record of events, such as who entered or exited, when, and how. Hard token, key fob, and door lock are not sufficient to meet the requirements of this question. A hard token is a device that generates a one-time password or code for authentication purposes. A key fob is a small device that can be attached to a key ring and used to unlock doors or start vehicles remotely. A door lock is a mechanism that secures a door from opening without a key or a code.
| Page 5 out of 148 Pages |
| Previous |