
- Email support@dumps4free.com

Topic 1: Exam Pool A
After clicking on a link in an email a Chief Financial Officer (CFO) received the following
error:
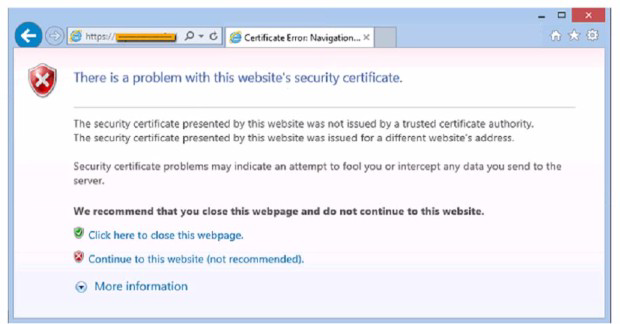
A. Update the browser's CRLs
B. File a trouble ticket with the bank.
C. Contact the ISP to report the CFCs concern
D. Instruct the CFO to exit the browser
Explanation:
The technician should update the browser’s CRLs first. The error message indicates that
the certificate revocation list (CRL) is not up to date. Updating the CRLs will ensure that the
browser can verify the authenticity of the bank’s website.
A technician has verified that a user's computer has a virus and the antivirus software is out of date. Which of the following steps should the technician take next?
A. Quarantine the computer.
B. Use a previous restore point.
C. Educate the end user about viruses.
D. Download the latest virus definitions.
A technician needs to replace a PC's motherboard. The technician shuts down the PC. Which of the following steps should the technician take next?
A. Turn off the monitor.
B. Remove the power cord.
C. Remove the PSU.
D. Remove the RAM modules.
Explanation: Removing the power cord is the first step to ensure the safety of the technician and the PC components. This will prevent any electrical shock or damage that may occur if the PC is still connected to a power source. The technician should also press the power button to drain any residual power from the capacitors.
A technician is modifying the default home page of all the workstations in a company. Which of the following will help to implement this change?
A. Group Policy
B. Browser extension
C. System Configuration
D. Task Scheduler
Explanation: Group Policy is a feature of Windows that allows administrators to centrally manage and configure the settings of computers and users in a domain network. Group Policy can be used to modify the default home page of all the workstations in a company by creating and applying a policy that specifies the desired URL for the home page. This way, the change will be automatically applied to all the workstations that are joined to the domain and receive the policy.
A user attempts to open some files, but a message appears stating that the files are encrypted. The user was able to access these files before without receiving this message and no changes have been made within the company. Which of the following has infected the computer?
A. Cryptominer
B. Phishing
C. Ransomware
D. Keylogger
Explanation:
Ransomware is malicious software that encrypts files on a computer, making them
inaccessible until a ransom is paid. In this case, the user was able to access the files
before without issue, and no changes have been made within the company, so it is likely
that the computer was infected with ransomware.
| Page 26 out of 148 Pages |
| Previous |