
- Email support@dumps4free.com

Topic 5: Exam Pool E
As a corporate technician, you are asked to evaluate several suspect email messages on a client's computer. Corporate policy requires he following:
. All phishing attempts must be reported.
. Future spam emails to users must be prevented. INSTRUCTIONS
Review each email and perform the following within the email:
. Classify the emails
. Identify suspicious items, if applicable, in each email
. Select the appropriate resolution
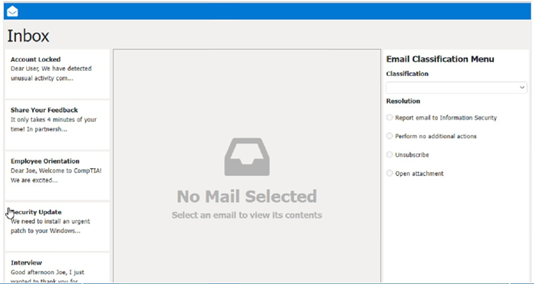
Answer: See the Full solution in Explanation below.
Explanation:
Classification: a) Phishing
This email is a phishing attempt, as it tries to trick the user into clicking on a malicious link that could compromise their account or personal information. Some suspicious items in this email are:
The email has a generic greeting and does not address the user by name.
The email has spelling errors, such as “unusal” and “Locaked”.
The email uses a sense of urgency and fear to pressure the user into clicking on the link.
The email does not match the official format or domain of the IT Help Desk at CompTIA.
The email has two black bat icons, which are not related to CompTIA or IT support.
The appropriate resolution for this email is A. Report email to Information Security. The user should not click on the link, reply to the email, or provide any personal or account information. The user should forward the email to the Information Security team or use a professional email form to report the phishing attempt. The user should also delete the email from their inbox and trash folder.
The suspicious items to select are:
b) From address
d) Hyperlinks
These items indicate that the email is not from a legitimate source and that the link is potentially malicious. The other items are not suspicious in this case, as the to address is the user’s own email and there are no attachments.
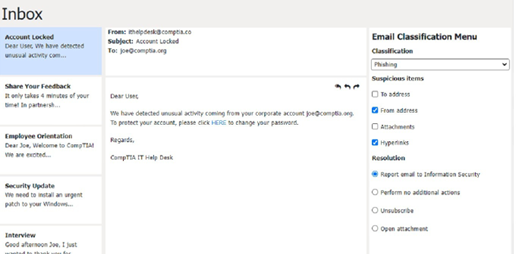
Classification: b) Spam
This email is a spam email, as it is an unsolicited and unwanted message that tries to persuade the user to participate in a survey and claim a reward. Some suspicious items in this email are:
The email offers a free wireless headphone as an incentive, which is too good to be true.
The email does not provide any details about the survey company, such as its name, address, or contact information.
The email contains an external survey link, which may lead to a malicious or fraudulent website.
The email does not have an unsubscribe option, which is required by law for commercial emails.
The appropriate resolution for this email is C. Unsubscribe. The user should look for an unsubscribe link or button at the bottom of the email and follow the instructions to opt out of receiving future emails from the sender. The user should also mark the email as spam or junk in their email client, which will help filter out similar emails in the future. The user should not click on the survey link, reply to the email, or provide any personal or financial information.
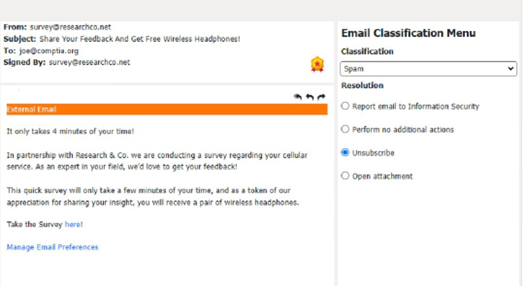
Classification: c) Legitimate
This email is a legitimate email, as it is from a trusted source and has a valid purpose. There are no suspicious items in this email, as the from address, the to address, the attachment, and the email body are all consistent and relevant. The appropriate resolution for this email is B. Perform no additional actions. The user can open the attachment and review the orientation material as instructed. The user does not need to report, unsubscribe, or delete this email.
Classification: a) Phishing
This email is a phishing attempt, as it tries to deceive the user into downloading and running a malicious attachment that could compromise their system or data. Some suspicious items in this email are:
The email has a generic greeting and does not address the user by name or username.
The email has an urgent tone and claims that a security patch needs to be installed immediately.
The email has an attachment named “patch1.exe”, which is an executable file that could contain malware or ransomware.
The email does not match the official format or domain of CompTIA Information Security.
The appropriate resolution for this email is A. Report email to Information Security. The user should not open the attachment, reply to the email, or provide any personal or account information. The user should forward the email to the Information Security team or use a professional email form to report the phishing attempt. The user should also delete the email from their inbox and trash folder.
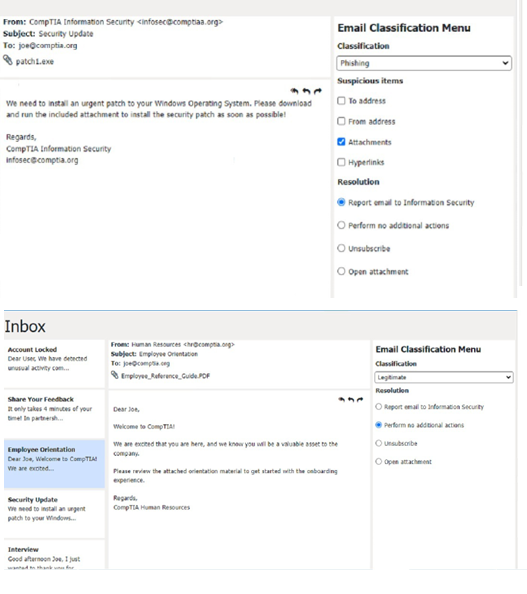
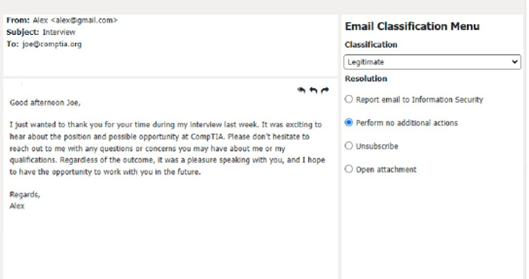
Classification: c) Legitimate
This email is a legitimate email, as it is from a trusted source and has a valid purpose. There are no suspicious items in this email, as the from address, the to address, and the email body are all consistent and relevant. The appropriate resolution for this email is B. Perform no additional actions. The user can reply to the email and thank the sender for the interview opportunity. The user does not need to report, unsubscribe, or delete this email.
Which of the following could be used to implement secure physical access to a data center?
A. Geofence
B. Alarm system
C. Badge reader
D. Motion sensor
Explanation:
Badge readers are used to implement secure physical access to a data center. They are
used to read the identification information on an employee’s badge and grant access to the data center if the employee is authorized2.
This system requires individuals to have an access badge that contains their identification
information or a unique code that can be scanned by a reader. After the badge is scanned,
the system compares the information on the badge with the authorized personnel database
to authenticate if the individual has the required clearance to enter that area. The other
options listed, such as a geofence, alarm system, or motion sensor are security measures
that may be used in conjunction with badge readers, but do not provide identification and
authentication features.
A user reports that a PC seems to be running more slowly than usual. A technician checks system resources, but disk, CPU, and memory usage seem to be fine. The technician sees that GPU temperature is extremely high. Which of the following types of malware is MOST likely to blame?
A. Spyware
B. Cryptominer
C. Ransormvare
D. Boot sector virus
Explanation:
The type of malware that is most likely to blame for a PC running more slowly than usual
and having an extremely high GPU temperature is a “cryptominer”. Cryptominers are a type
of malware that use the resources of a computer to mine cryptocurrency. This can cause
the computer to run more slowly than usual and can cause the GPU temperature to rise.
Spyware is a type of malware that is used to spy on a user’s activities, but it does not
typically cause high GPU temperatures. Ransomware is a type of malware that encrypts a
user’s files and demands payment to unlock them, but it does not typically cause high GPU
temperatures. Boot sector viruses are a type of malware that infects the boot sector of a
hard drive, but they do not typically cause high GPU temperatures12.
A technician has been tasked with installing a workstation that will be used tor point-of-sale transactions. The point-of-sale system will process credit cards and loyalty cards. Which of the following encryption technologies should be used to secure the workstation in case of theft?
A. Data-in-transit encryption
B. File encryption
C. USB drive encryption
D. Disk encryption
Explanation:
Disk encryption should be used to secure the workstation in case of theft. Disk encryption
can help to protect data on the hard drive by encrypting it so that it cannot be accessed
without the correct encryption key.
A technician wants to enable BitLocker on a Windows 10 laptop and is unable to find the BitLocker Drive Encryption menu item in Control Panel. Which of the following explains why the technician unable to find this menu item?
A. The hardware does not meet BitLocker's minimum system requirements.
B. BitLocker was renamed for Windows 10.
C. BitLocker is not included on Windows 10 Home.
D. BitLocker was disabled in the registry of the laptop
Explanation:
BitLocker is only available on Windows 10 Pro, Enterprise, and Education
editions1. Therefore, the technician is unable to find the BitLocker Drive Encryption menu
item in Control Panel because it is not included in the Windows 10 Home edition1.
| Page 15 out of 148 Pages |
| Previous |