
- Email support@dumps4free.com

A network engineer discovers that a foreign government hacked one of the defense contractors in their home country and stole intellectual property. What is the threat agent in this situation?
A.
the intellectual property that was stolen
B.
the defense contractor who stored the intellectual property
C.
the method used to conduct the attack
D.
the foreign government that conducted the attack
the foreign government that conducted the attack
A network engineer discovers that a foreign government hacked one of the defense contractors in their home country and stole intellectual property. What is the threat agent in this situation?
A.
the intellectual property that was stolen
B.
the defense contractor who stored the intellectual property
C.
the method used to conduct the attack
D.
the foreign government that conducted the attack
the foreign government that conducted the attack
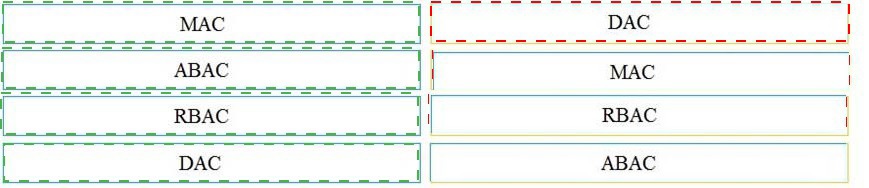
Drag and drop the access control models from the left onto the correct descriptions on the right.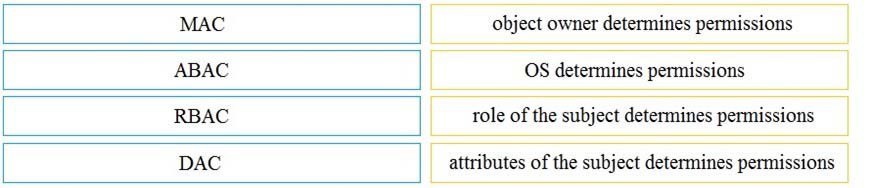
Which security principle requires more than one person is required to perform a critical task?
A.
least privilege
B.
need to know
C.
separation of duties
D.
due diligence
separation of duties
Which incidence response step includes identifying all hosts affected by an attack'?
A.
post-incident activity
B.
detection and analysis
C.
containment eradication and recovery
D.
preparation
post-incident activity
| Page 3 out of 37 Pages |
| Previous |